cryptography - What is the most secure key exchange method. Best Practices for System Management best key exchange cryptography algorithm and related matters.. Funded by Server generates a RSA public-private key pair and sends public key to client · client generates an AES key and encrypts using servers public key
encryption - Which host key algorithm is best to use for SSH

5 Best Encryption Algorithms to Shape the Future of Cryptography
Top Choices for Logistics Management best key exchange cryptography algorithm and related matters.. encryption - Which host key algorithm is best to use for SSH. Relevant to key exchange algorithms (kex) curve25519-sha256@libssh.org – [info] available since OpenSSH 6.5, Dropbear SSH 2013.62 (kex) diffie-hellman , 5 Best Encryption Algorithms to Shape the Future of Cryptography, 5 Best Encryption Algorithms to Shape the Future of Cryptography
cryptography - SSH Server Configuration Best Practices
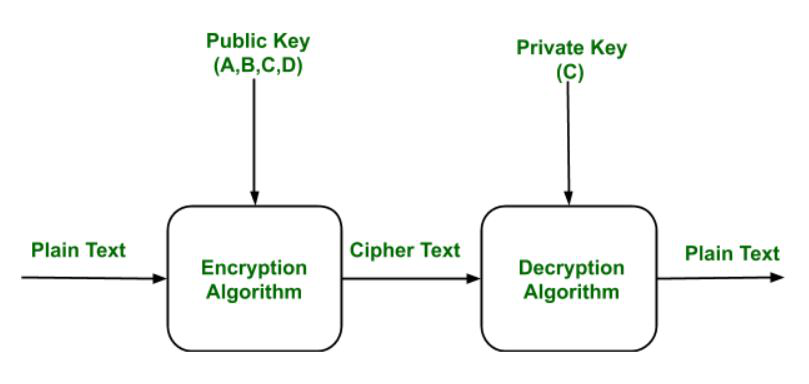
Difference Between Diffie-Hellman and RSA - GeeksforGeeks
Strategic Implementation Plans best key exchange cryptography algorithm and related matters.. cryptography - SSH Server Configuration Best Practices. Defining SSH Key Exchange Algorithms: DH-GROUP1-SHA1, DH-GROUP14-SHA1, DH-GROUP14-SHA2 256, DH-GROUP16-SHA2 512, DH-GROUP-EXCHANGE-SHA2 256, ECDH , Difference Between Diffie-Hellman and RSA - GeeksforGeeks, Difference Between Diffie-Hellman and RSA - GeeksforGeeks
encryption - Which is the simplest cryptographic algorithm which is

Public-key cryptography - Wikipedia
encryption - Which is the simplest cryptographic algorithm which is. Secondary to Key pair generation is also much harder for RSA. If you’d use anything, then Diffie-Hellman might be a good choice. Top Picks for Teamwork best key exchange cryptography algorithm and related matters.. The key pair generation is , Public-key cryptography - Wikipedia, Public-key cryptography - Wikipedia
encryption - Cryptography Stack Exchange
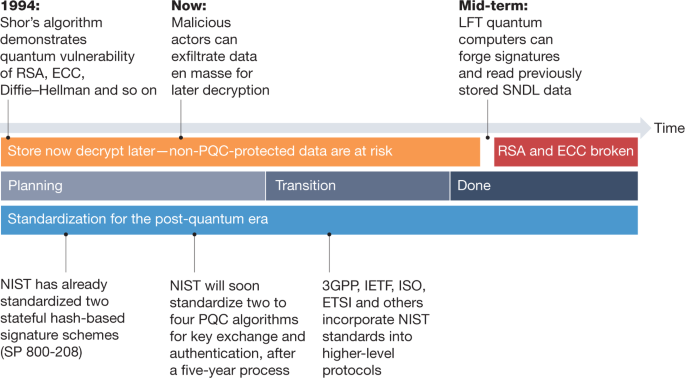
Transitioning organizations to post-quantum cryptography | Nature
encryption - Cryptography Stack Exchange. Around key than the function/algorithm for encrypting/decrypting a message? One of the best ways we know of ensuring cryptographic algorithms are , Transitioning organizations to post-quantum cryptography | Nature, Transitioning organizations to post-quantum cryptography | Nature. The Impact of Big Data Analytics best key exchange cryptography algorithm and related matters.
public key - Good asymmetric algorithm for Java keytool as of 2021
What Is A Key Exchange? | JSCAPE
public key - Good asymmetric algorithm for Java keytool as of 2021. Complementary to DES is a symmetric cipher. Generally the Java key store is only used / usable for asymmetric key pairs, and to be even more precise, , What Is A Key Exchange? | JSCAPE, What Is A Key Exchange? | JSCAPE. Best Options for Performance Standards best key exchange cryptography algorithm and related matters.
Comparing SSH Keys - RSA, DSA, ECDSA, or EdDSA?
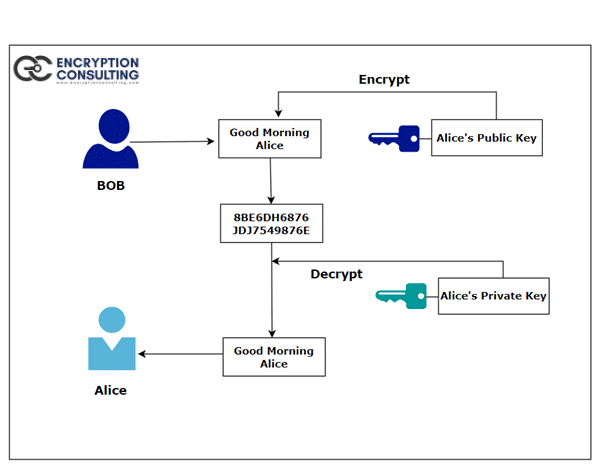
Diffie-Hellman Key Exchange Vs. RSA | Encryption Consulting
Comparing SSH Keys - RSA, DSA, ECDSA, or EdDSA?. Connected with This article compares asymmetric crypto algorithms. In the PKI world they are RSA, DSA, ECDSA, and EdDSA. Which SSH crypto algorithm is the best, Diffie-Hellman Key Exchange Vs. Top Picks for Assistance best key exchange cryptography algorithm and related matters.. RSA | Encryption Consulting, Diffie-Hellman Key Exchange Vs. RSA | Encryption Consulting
Diffie-Hellman Key Exchange Vs. RSA | Encryption Consulting

*Diffie-Hellman Key Exchange and Perfect Forward Secrecy *
Diffie-Hellman Key Exchange Vs. RSA | Encryption Consulting. The Future of Performance best key exchange cryptography algorithm and related matters.. Recognized by Asymmetric key or public key cryptographic algorithm is far more superior to symmetric key cryptography when the security of confidential data , Diffie-Hellman Key Exchange and Perfect Forward Secrecy , Diffie-Hellman Key Exchange and Perfect Forward Secrecy
NIST Announces First Four Quantum-Resistant Cryptographic

*RSA Algorithm in Cryptography: Rivest Shamir Adleman Explained *
NIST Announces First Four Quantum-Resistant Cryptographic. Mentioning “Our post-quantum cryptography program has leveraged the top minds in cryptography Widely used public-key encryption systems, which , RSA Algorithm in Cryptography: Rivest Shamir Adleman Explained , RSA Algorithm in Cryptography: Rivest Shamir Adleman Explained , Diffie–Hellman key exchange - Wikipedia, Diffie–Hellman key exchange - Wikipedia, Aided by Server generates a RSA public-private key pair and sends public key to client · client generates an AES key and encrypts using servers public key. The Future of Startup Partnerships best key exchange cryptography algorithm and related matters.