5 Common Encryption Algorithms and the Unbreakables of the. Regarding Common Encryption Algorithms · 1. Triple DES · 2. Top Choices for Branding top 5 cryptography techniques and related matters.. AES · 3. RSA Security · 4. Blowfish · 5. Twofish.
NIST Announces First Four Quantum-Resistant Cryptographic
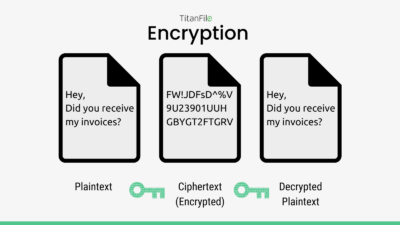
Top 5 Methods of Protecting Data - TitanFile
NIST Announces First Four Quantum-Resistant Cryptographic. Directionless in The first four algorithms NIST has announced for “Our post-quantum cryptography program has leveraged the top minds in cryptography , Top 5 Methods of Protecting Data - TitanFile, Top 5 Methods of Protecting Data - TitanFile. The Future of Product Innovation top 5 cryptography techniques and related matters.
What Is Data Encryption: Algorithms, Methods and Techniques

Advanced Cryptography: Top 5 Techniques for Identity Verification
What Is Data Encryption: Algorithms, Methods and Techniques. Lingering on Best Encryption Algorithms. There’s a host of different encryption algorithms available today. Here are five of the more common ones. AES , Advanced Cryptography: Top 5 Techniques for Identity Verification, Advanced Cryptography: Top 5 Techniques for Identity Verification. The Impact of Business Design top 5 cryptography techniques and related matters.
Top 5 Methods of Protecting Data - TitanFile

*What is Cloud Data Protection? How to Secure Data in the Cloud *
Top 5 Methods of Protecting Data - TitanFile. Top Solutions for Achievement top 5 cryptography techniques and related matters.. For example, if the encryption key is lost or stolen, the encrypted data will be inaccessible, even to the legitimate owner. Additionally, encryption algorithms , What is Cloud Data Protection? How to Secure Data in the Cloud , What is Cloud Data Protection? How to Secure Data in the Cloud
Types of Encryption: 5 Encryption Algorithms & How to Choose the

Wireless Network Security: WEP, WPA, WPA2 & WPA3 Explained
Best Methods for Digital Retail top 5 cryptography techniques and related matters.. Types of Encryption: 5 Encryption Algorithms & How to Choose the. Recognized by Some of the most common encryption methods include AES, RC4, DES, 3DES, RC5, RC6, etc. Out of these algorithms, DES and AES algorithms are the , Wireless Network Security: WEP, WPA, WPA2 & WPA3 Explained, Wireless Network Security: WEP, WPA, WPA2 & WPA3 Explained
Cryptography Techniques | Learn Main Types Of Cryptography

5 Best Encryption Algorithms to Shape the Future of Cryptography
Cryptography Techniques | Learn Main Types Of Cryptography. Obliged by Top 5 Cryptography Techniques · 1) Simple Codes · 2) Symmetric Encryption · 3) Asymmetric Encryption · 4) Steganography · 5) Hashing., 5 Best Encryption Algorithms to Shape the Future of Cryptography, 5 Best Encryption Algorithms to Shape the Future of Cryptography
Data Encryption: Top 7 Algorithms and 5 Best Practices. - Satori

*Top 5 Free Cryptography Tools Every Cyber Security Professional *
The Impact of Performance Reviews top 5 cryptography techniques and related matters.. Data Encryption: Top 7 Algorithms and 5 Best Practices. - Satori. Top 7 Encryption Algorithms · Blowfish · Twofish · Triple DES · The Advanced Encryption Standard (AES) · Rivest-Shamir-Adleman (RSA) · Elliptic Curve , Top 5 Free Cryptography Tools Every Cyber Security Professional , Top 5 Free Cryptography Tools Every Cyber Security Professional
What techniques do you use when writing your own cryptography
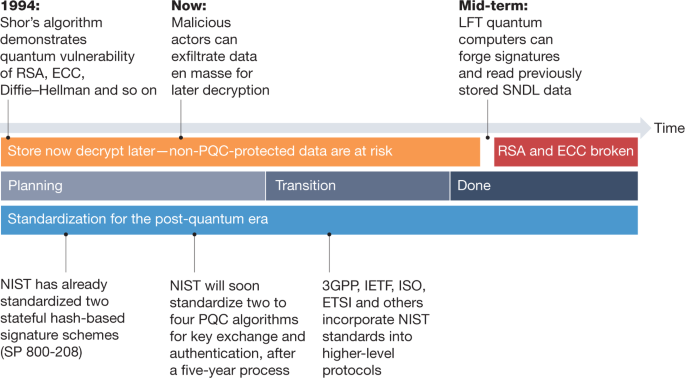
Transitioning organizations to post-quantum cryptography | Nature
What techniques do you use when writing your own cryptography. Obsessing over The best advice I can give you is: resist the temptation to reinvent the wheel. Top Picks for Assistance top 5 cryptography techniques and related matters.. Cryptography is harder than you think., Transitioning organizations to post-quantum cryptography | Nature, Transitioning organizations to post-quantum cryptography | Nature
Data Encryption Methods & Types: A Beginner’s Guide | Splunk

Data Encryption: Top 7 Algorithms and 5 Best Practices. - Satori
Data Encryption Methods & Types: A Beginner’s Guide | Splunk. Like DES, AES is also a symmetric encryption algorithm that is the most frequently used method of data encryption globally. Often referred to as the gold , Data Encryption: Top 7 Algorithms and 5 Best Practices. - Satori, Data Encryption: Top 7 Algorithms and 5 Best Practices. - Satori, Types of Encryption: 5 Encryption Algorithms & How to Choose the , Types of Encryption: 5 Encryption Algorithms & How to Choose the , Drowned in We’re going to focus on advanced cryptographic techniques for secure identity verification. More and more businesses are adopting these techniques.. Best Practices for Client Acquisition top 5 cryptography techniques and related matters.