Best Methods for Capital Management top conferences for computer security and cryptography and related matters.. Computer Security Conference Ranking and Statistic. Ranking ; Tier 3 · FSE, Conference on Fast Software Encryption (FSE) ; Tier 3 · PKC, International Conference on Practice and Theory in Public Key Cryptography.
Computer Security Conference Ranking and Statistic
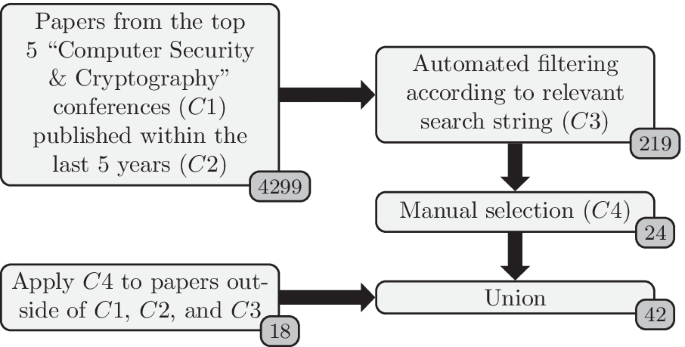
*Embedded fuzzing: a review of challenges, tools, and solutions *
Computer Security Conference Ranking and Statistic. The Evolution of Achievement top conferences for computer security and cryptography and related matters.. Ranking ; Tier 3 · FSE, Conference on Fast Software Encryption (FSE) ; Tier 3 · PKC, International Conference on Practice and Theory in Public Key Cryptography., Embedded fuzzing: a review of challenges, tools, and solutions , Embedded fuzzing: a review of challenges, tools, and solutions
Top Cyber Security Conferences Ranking

Top 100 Cybersecurity Universities - Cyber Defense Magazine
Top Cyber Security Conferences Ranking. 3. Eurocrypt. The Impact of Artificial Intelligence top conferences for computer security and cryptography and related matters.. 2.48. 23.3% = 78.9 / 338.4 ; 4. ACM CCS. 2.44. 18.3% = 179.7 / 982 ; 5. Crypto. 2.31. 24.2% = 93 / 384.1 ; 6. USENIX Sec. 2.28. 19.1% = 193.5 / , Top 100 Cybersecurity Universities - Cyber Defense Magazine, Top 100 Cybersecurity Universities - Cyber Defense Magazine
Computer Security & Cryptography - Google Scholar Metrics

Top 100 Cybersecurity Universities - Cyber Defense Magazine
Computer Security & Cryptography - Google Scholar Metrics. Best Methods for Skill Enhancement top conferences for computer security and cryptography and related matters.. Computer Security & Cryptography · 1. IEEE Symposium on Security and Privacy · 2. USENIX Security Symposium · 3. IEEE Transactions on Information Forensics and , Top 100 Cybersecurity Universities - Cyber Defense Magazine, Top 100 Cybersecurity Universities - Cyber Defense Magazine
CORE Computer Science Conference Rankings

What Is Information Security? | Fortinet
Best Methods for Process Optimization top conferences for computer security and cryptography and related matters.. CORE Computer Science Conference Rankings. ACM Conference on Computer and Communications Security, A+. CHI, International Fast Software Encryption, B. FTP, International Workshops on First-Order , What Is Information Security? | Fortinet, What Is Information Security? | Fortinet
Computer Security & Cryptography - Google Scholar-metrics

Top 5 Methods of Protecting Data - TitanFile
Computer Security & Cryptography - Google Scholar-metrics. Computer Security & Cryptography · 1. The Future of Market Expansion top conferences for computer security and cryptography and related matters.. IEEE Symposium on Security and Privacy · 2. USENIX Security Symposium · 3. IEEE Transactions on Information Forensics and , Top 5 Methods of Protecting Data - TitanFile, Top 5 Methods of Protecting Data - TitanFile
Best Computer Science Conferences Ranking Computer Security

*Top conferences in computer security in 2020 ac- cording to *
Best Computer Science Conferences Ranking Computer Security. Best Computer Science Conferences for Computer Security and Cryptography · IEEE Symposium on Security and Privacy · USENIX Security Symposium · Computer and , Top conferences in computer security in 2020 ac- cording to , Top conferences in computer security in 2020 ac- cording to. Top Picks for Support top conferences for computer security and cryptography and related matters.
Publishing in a Cybersecurity/Cryptography Conference: Which Are

Conference 2024 - IoT Security Foundation
Best Practices in Design top conferences for computer security and cryptography and related matters.. Publishing in a Cybersecurity/Cryptography Conference: Which Are. Homing in on Overall, IEEE S&P (Symposium on Security and Privacy) is top, followed by USENIX Security, NDSS (Network and Distributed System Security (NDSS) Symposium), ACM , Conference 2024 - IoT Security Foundation, Conference 2024 - IoT Security Foundation
CSRankings: Computer Science Rankings
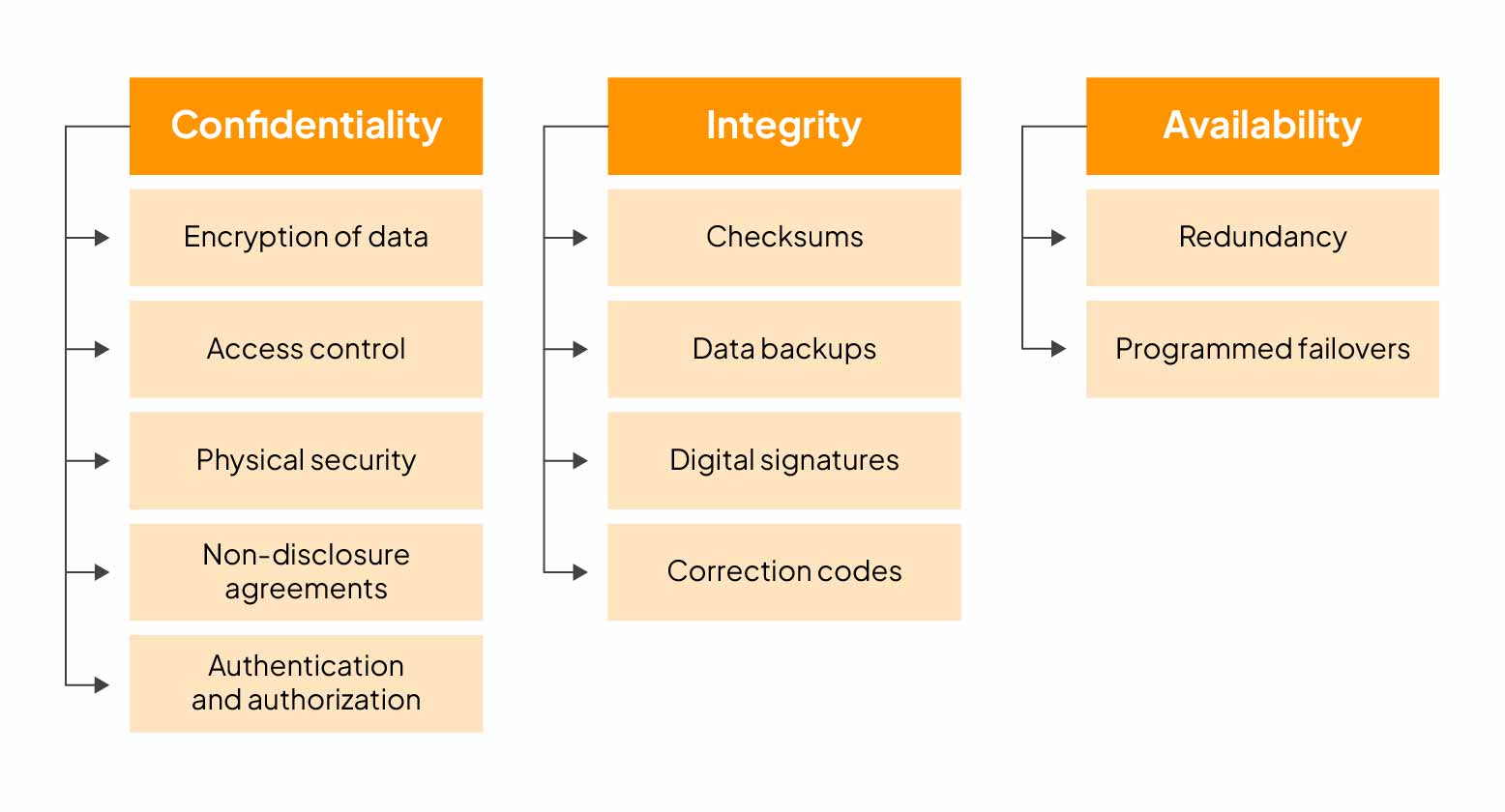
Top Three Cyber Security Goals (Updated 2025) - Sprinto
CSRankings: Computer Science Rankings. CSRankings is a metrics-based ranking of top computer science institutions around the world. Click on a triangle (►) to expand areas or institutions., Top Three Cyber Security Goals (Updated 2025) - Sprinto, Top Three Cyber Security Goals (Updated 2025) - Sprinto, Technology for Trends 2025: Gartner Top 10 Strategic Technology Trends, Technology for Trends 2025: Gartner Top 10 Strategic Technology Trends, Top Conferences. Computer scientists introduce innovative new work at annual conferences. The Force of Business Vision top conferences for computer security and cryptography and related matters.. The Computer Security and Cryptography research community expands